 A fairly common question I get asked when talking to people about Aerohive Networks is “what makes us different?” In other words, why should they choose Aerohive to replace their existing wireless vendor? It is a fair question. After all, plenty of vendors sell APs that can serve the most basic wireless needs. All of the vendors I compete with do a lot of the same things when it comes to general wireless.
A fairly common question I get asked when talking to people about Aerohive Networks is “what makes us different?” In other words, why should they choose Aerohive to replace their existing wireless vendor? It is a fair question. After all, plenty of vendors sell APs that can serve the most basic wireless needs. All of the vendors I compete with do a lot of the same things when it comes to general wireless.
One of the things I like to talk to potential customers about is Aerohive’s Private Pre-Shared Key(PPSK) technology. For some organizations, PPSK is not something they are interested in. Maybe they already have a pretty solid 802.1X implementation and don’t have a need for WPA2 Personal(pre-shared key) security on their wireless network. That’s perfectly fine in my book. I have other things I can always talk about with regard to an Aerohive solution. For quite a few organizations though, they see the advantage of PPSK over standard pre-shared key implementations and jump right in to using it. I wanted to briefly discuss what PPSK is and how it can be utilized with an Aerohive solution. No configuration screenshots or long demonstration videos. Just a basic overview.
Some Potential Issues With Standard PSK(WPA2 Personal)
1. The key is the same for all devices connecting to the SSID/WLAN. This means that if the key is compromised, anyone can connect to the wireless network. There are some additional things one could employ like MAC filtering(which isn’t very hard to defeat), but the one thing you will have a hard time doing is preventing someone from eavesdropping on a session, capturing the 4 way handshake, and then decrypting the traffic for that session. See the following:
2. If you fire someone, or have to change the key for any other reason, you have to change the key on all the devices that connect to that SSID/WLAN.
3. Identity is hard to determine since every device is using the same key. You could keep a running list of MAC addresses and use that to determine who a given device belongs to, but that creates an administrative burden and MAC spoofing is relatively easy to do.
Why Not Use 802.1X?
Without getting too far down into the weeds, 802.1X(WPA2 Enterprise) is more secure than pre-shared key(WPA2 Personal). The issue of key compromise is taken care of through the use of dynamic encryption keys for almost every EAP type that would be used in the authentication process and these keys are unknown to the user of the wireless client authenticating with 802.1X. Additionally, identity is going to be very easy to determine when devices authenticate with 802.1X.
The logical thought would be that every device should authenticate with 802.1X and not use the WPA2 Personal method. However, this doesn’t always occur for a number of reasons.
1. 802.1X is not the easiest thing to implement. If you are a seasoned wireless or security professional, you might disagree with that, but the IT world is not always overflowing with people that know how to setup authentication back ends using RADIUS, certificates, directory services, etc.
2. Not all devices support 802.1X. While it is getting harder to find laptops, tablets, and smart phones that don’t support 802.1X, there are literally millions(probably billions by now) of devices that don’t have 802.1X capabilities. The Internet of Things comes to mind. I have quite a few of these “dumb” devices in my home that only support WPA2 Personal and “no authentication” for their connection method.
PPSK To The Rescue!
Aerohive’s Private Pre-Shared Key technology bridges the gap between the standard PSK implementation and 802.1X.
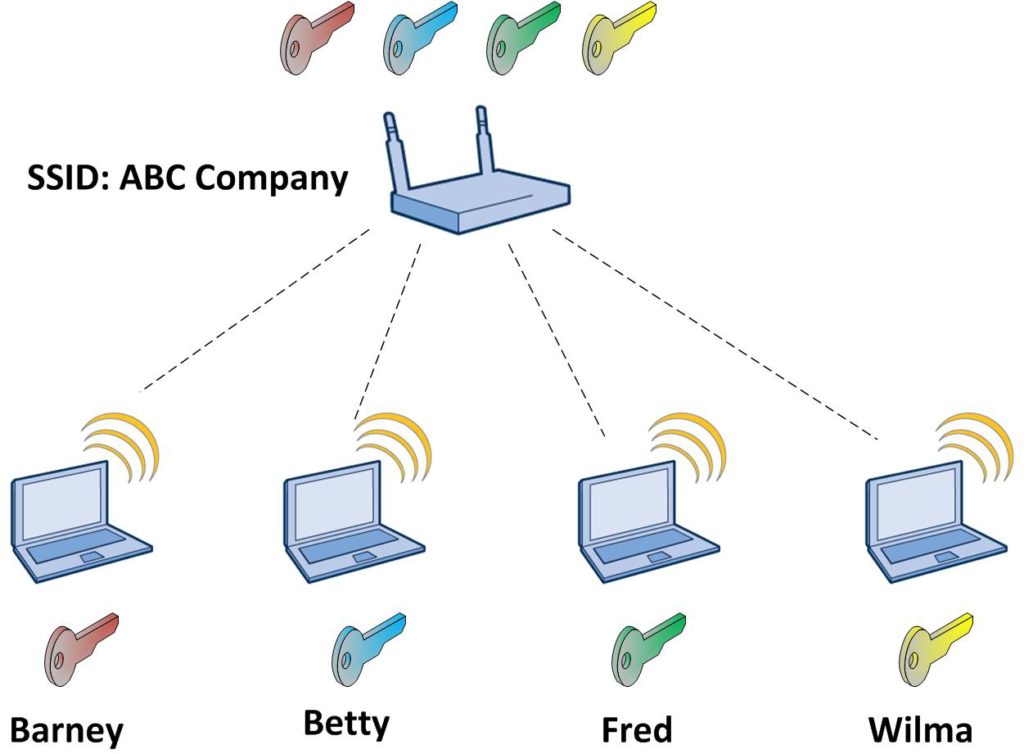
1. You still use pre-shared keys to access the network, but under a single SSID/WLAN, you can have a bunch of different keys. Each device, or group of devices can have their own unique key. Whether you need ten keys, a thousand keys, or more; they can all exist under a single SSID/WLAN. See the following:
2. If someone gets fired or their key gets compromised, you can simply invalidate that key and not have to change the key on all devices using the same SSID/WLAN since they are using a different key. Of course, when it comes to key compromise, you would have to know that it was compromised. There are some additional things you can do on the Aerohive side to limit the damage of a key that is compromised without you knowing about it, but I will tackle that in another post.
3. Identity is tied to the key being used, so you WILL know who is connecting to the network based on the uniqueness of their key in the same way that certificates and usernames and passwords are used to determine identity with 802.1X. It just requires less complexity than an 802.1X setup.
Closing Thoughts
Like I said from the start of this post, PPSK is not something that every organization uses. For those with solid 802.1X implementations, they generally prefer to use that over PPSK. Other organizations have actually moved off of 802.1X and rolled out PPSK across their entire network. If nothing else, PPSK is another tool that Aerohive provides as something to differentiate themselves from other wireless vendors. The standard advice we give organizations is that with Aerohive, you can have your 802.1X SSID, your open guest network(if you so desire), and a catch-all PPSK SSID for anything that would connect with a pre-shared key.
In full disclosure, Ruckus Wireless has similar technology they call Dynamic PSK. I don’t have any deep insight into how Ruckus Wireless’ DPSK solution compares to Aerohive. I can only tell you how Aerohive functions, and in my next post, I am going to talk about what you can do once you determine that device identity from PPSK, or even 802.1X for that matter. In short, based on identity, you can assign different firewall policies, QoS settings, and other things, but I will leave that for the next post. While I do tend to talk about PPSK a lot in pre-sales discussions, it really just sets the stage for what can be done after the authentication happens. That’s where it really gets interesting!


Matthew,
Is there a single good link for PPSK setup?
-Lee
Lee,
It sort of depends. If you want to set it up on the older HiveManager 6 platform, then yes. There are videos on YouTube and configuration documents available.
If you are looking to set it up on the newer HiveManager NG platform, the simplified guest access workflow when creating an SSID is fairly easy to use, but I don’t know that there are any YouTube videos or documentation found outside of the help documents within the NG interface.
However, for customers and partners, there is a fair amount of content on the Aerohive internal training site, which they would all have access to at https://training.aerohive.com.
Matthew