I spend a lot of time pouring over vendor solutions. A lot. Unfortunately, I don’t specialize in one area like wireless, security, storage, voice, etc. I am more of a network generalist. Because of that, I tend to focus on the big companies or those who fill a certain niche. There are just too many vendors to keep track of. Because of that, I seem to have missed Meraki. Thank goodness for Wireless Field Day 2! For an in depth recap of the WFD2 visit to Meraki, read Tom Hollingsworth’s post here.
I spend a lot of time pouring over vendor solutions. A lot. Unfortunately, I don’t specialize in one area like wireless, security, storage, voice, etc. I am more of a network generalist. Because of that, I tend to focus on the big companies or those who fill a certain niche. There are just too many vendors to keep track of. Because of that, I seem to have missed Meraki. Thank goodness for Wireless Field Day 2! For an in depth recap of the WFD2 visit to Meraki, read Tom Hollingsworth’s post here.
It’s not that I was completely ignorant of them. I’d seen some of their advertisements. I knew that they sold wireless gear. I knew that they had some switches and firewalls. Everything was managed by the “cloud”. I took all that into consideration and thought: “Yay. Another vendor shilling for the “cloud”. As if we didn’t have enough already.” That was my thoughts on Meraki coming into Wireless Field Day 2. I work for a VAR that sells Cisco, HP, Aerohive, Brocade, Juniper, and a ton of other vendors. We have a variety of wireless choices at our disposal. I can sell a product for almost any environment. In short, I can work with all sorts of “it depends” scenarios. That should help explain some of my skepticism.
That doesn’t mean I was opposed to hearing Meraki’s pitch. I LOVE talking to vendors no matter the size of the company or the particular area they focus on. I firmly believe that every vendor has something to offer. They ALL employ smart people.
So that’s where I was at on Thursday, January26th when we pulled up to the Meraki headquarters in San Francisco. I was a skeptical non-believer. We walked through their offices and it felt 100% like a tech startup. Lots of young people typing away on large screen Macs. Plenty of flair attached to desks of varying heights. A few dogs wandering around. Snacks galore in their break area(which also included a few kegs of beer). All the things that scream: “You want to come to work.” Nothing like the usual corporate environments where cubical walls run high, dress codes are enforced, and the only semblance of a corporate perk is free coffee or a meager selection of carbonated beverages. Still, I was skeptical. I’ve seen this before. It is replayed “ad nauseum” across the entire Silicon Valley landscape.
The more I listened to the people from Meraki talk, the more I began to change my mind about them. We all asked a fair amount of questions. They answered them with a fair amount of candor. They also did a demonstration of their management platform. During this demonstration, I couldn’t help but think how polished the management interface looked. It was full of features, yet didn’t seem cluttered. It wasn’t a canned demo either. Below is a video of Pablo Estrada from Meraki walking us through the wireless product. He also took a little time showing us the switch and firewall management piece as well.
Live demonstrations of Meraki Wi-Fi gear with Pablo Estrada from Stephen Foskett on Vimeo.
In addition to the extensive demonstration that Pablo did, one of the delegates from WFD2, Daniel Cybulskie, put together an article and video on Meraki’s Device Manager product. You can access it here.

Wireless
Their wireless product set is very easy to understand. A few AP models for indoor and a few for outside. They have all the major features other vendors have. WIPS, RTLS, spectrum analysis, RRM, 802.1x, device fingerprinting, etc. Everything is managed through the MCC(Meraki Cloud Controller). After our initial discussions at the Meraki headquarters, it seemed as if their controller wasn’t very controller-like at all. If you lost your connection to the MCC(ie the Internet), you could still authenticate new users provided your RADIUS box was local. Your captive portal would also continue working for guest access provided you hosted that locally. With a lot of the other solutions out there, this wasn’t the case. If you lost your link to the controller, you could still function, but no new client connections could happen.
Could this be another controller-less solution? After all, the MCC seemed to be more management plane oriented and less control plane oriented. Then, the mystery was solved. RRM didn’t work 100% without the connection to the MCC. In effect, layer 3 roaming was dead without the MCC link. However, we were informed that Meraki is working on making that functionality available locally(read the “Comments” section in this link). At some point in the future, you can lose the MCC link and still be able to roam via layer 3. I suspect this isn’t a big deal in some of the areas Meraki is prevalent in(ie retail), but can be an issue in the larger networks like educational institutions, hospitality, etc. Once the layer 3 roaming piece is worked out, Meraki will be a lot closer to the controller-less solution that Aerohive has been alone in for the past couple of years. Ideally, most decent sized networks will have redundant Internet connections. You could even buy a cheap DSL or cable modem circuit and only use it for backup connectivity to the MCC should your primary circuit fail. DSL and cable are cheap compared to a full blown redundant Internet circuit for a medium to large network. I am not entirely sure of the bandwidth requirements, but I can’t imagine they are huge given the fact that all data plane traffic stays local and quite a few of the control plane functions can stay local as well.

But Wait……..There’s More!
If one were to simply look at the wireless portion of Meraki, you would miss out. As of today, they are selling their own wired switches and firewalls. This is where I think they start to differentiate themselves from other companies even more. These devices are also managed over the Internet. The switches are basically 24 or 48 x 1Gbps interfaces. All wire speed/non-blocking. You can get them with or without PoE and they support 802.3af and 802.3at for your devices requiring a bit more power. Oh, and all ports can provide power at once if need be, but the limitation on the switch(24 and 48 port) is 380W in total.
There are some additional limitations on the switching side. They do provide 10Gbps uplinks from the switches, but it appears they are only doing so with short-haul multi-mode optics. I suspect this is because most of their customers are going to use short haul optics if any optics at all. In my opinion, these switches are not going to be dropped into a network to run as a core or distribution switch unless it is a rather small environment.

Yes. There’s Still More!
Not to be content with basic wired/wireless products, Meraki also has a decent firewall/UTM/router/call-it-what-you-will offering. Ranging from 100Mbps to 2Gbps stateful firewall throughput, they have a box that can meet most organization’s needs at least from a throughput perspective. As with any other vendor, when you spin up VPN connectivity, throughput drops like a rock. I suspect other features cause a performance hit as well, but those numbers aren’t displayed. That isn’t unique to Meraki. No other vendor that I know of will openly tell you how poorly their box runs when you turn all the features on. Why would they? Marketing isn’t in the business of highlighting the negatives. 🙂
A firewall is a firewall right? Not these days. If you want to differentiate yourself from the others, you need to have some serious application intelligence. A big part of what makes PaloAlto Networks a good firewall vendor is their ability to understand a ton of applications and affect throughput based on that understanding instead of the usual IP address and port access rules. Barracuda Networks can do this too with their Next Generation firewall as does Check Point with their latest and greatest offering. The Meraki firewall is able to do substantial application recognition and when paired with device fingerprinting, you can give users an experience that they will either love you for, or hate you for. In short, you have some serious options. Allow iPads to access Facebook, but prohibit laptops. Those kinds of things.
Apparently, that wasn’t enough for Meraki, so they took their firewalls to the next level. They included content filtering, routing, WAN optimization, link bonding, and automatic VPN creation.
The VPN portion looks to be pretty straightforward. They can create IPsec tunnels between your remote sites with a single click. I’ve built massive numbers of VPN connections over the years. However, I have never built one with a single click. Obviously, since all these devices are managed over the Internet, it can send down the appropriate phase1/2 parameters that you normally enter manually on each end of the connection. Very quick and efficient provided you are using Meraki gear on both sides.
The link bonding is really just a way of aggregating dissimilar connections so that you can perform basic load balancing and also have failover without having to employ a large amount of devices to support it all. Barracuda Networks has a similar product. This isn’t a service that a large enterprise customer would necessarily employ as they are going to use redundant hardware and other mechanisms to control the flow of traffic. I can see the benefit of this for the medium to smaller customers. Especially considering it doesn’t cost you any more money. In fact, the only increased licensing charge appears to be for content filtering, client VPN connectivity, and anti-virus.
I saw a bit of the content filtering during the product demo at the Meraki headquarters. It appears to be fairly in depth like most decent content filters are. You can filter by category, end user, etc. Nothing too exciting there, but a nice feature to have considering other vendors have separate appliances you have to install for this type of service.
The one thing out of all of these features that caught my eye was the WAN optimization piece. The low end MX60 has 100MB of cache. The other models all have 1TB of cache on a SATA drive with the exception of the large MX600. It has 4TB in a RAID configuration. That’s a lot of space for WAN optimization cache. If you look at Riverbed Steelheads, you have to get the 5050H to even get 800GB of cache storage. To get 4TB or more with Riverbed, you have to buy the largest box they sell, the 7050M. I can assure you that box costs 4 times or more of the price of the MX600. I would be willing to bet the Riverbed Steelheads will outperform the Meraki MX boxes from a WAN optimization perspective, but considering you get the WAN optimization for no additional fee, it would be worthwhile to use it even if the gain was minimal. Meraki states you can get up to 99% intersite bandwidth reduction using their WAN optimization and that you can accelerate CIFS, FTP, HTTP, and TCP traffic by up to 209 times the non-accelerated rate. Of course, that all depends on a variety of factors. I wouldn’t count on seeing those kinds of performance numbers outside of pristine lab scenarios, but again, it’s WAN optimization without the price tag of the larger vendors.
That covers the 3 main Meraki lines. Wireless, wired, and security. A product set that is easy to remember. Now how about pricing? What does a Meraki network cost? Thankfully, you can find that out before you even pick up the phone or send out an e-mail to their sales staff. They actually have a fairly decent pricing tool right on their web site. The cost for each AP, switch, and MX firewall is shown along with licensing, maintenance, etc. This is something I wish more vendors would do as it shows the customer right up front what their costs are going to be. If they get it cheaper, then even better, but at least they know how much they should budget for initially. What makes the pricing tool even more interesting is that they compare it to the cost of comparable Cisco products. They actually give the corresponding Cisco part number and the associated cost.
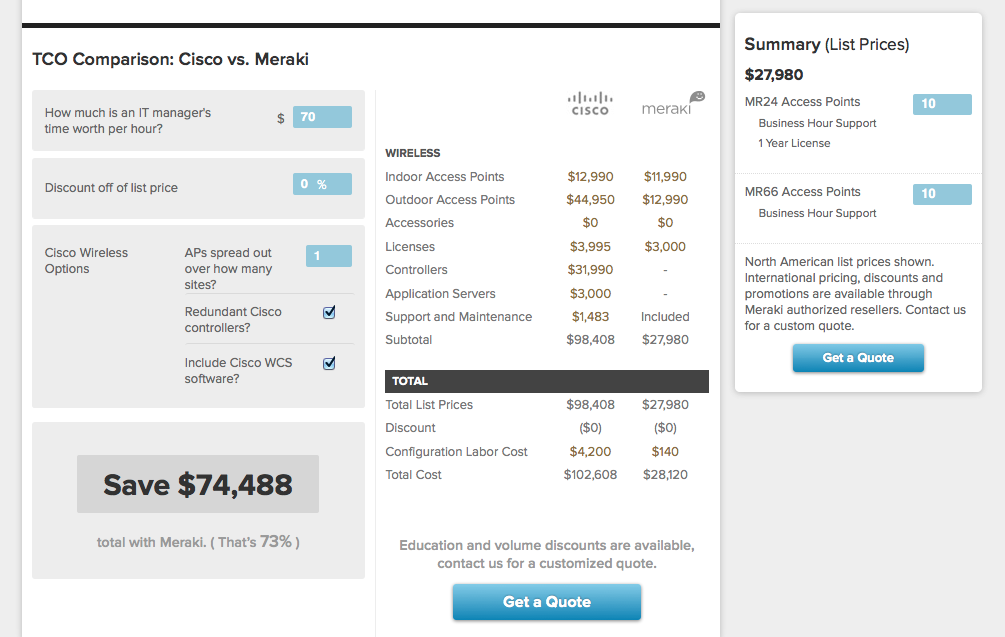
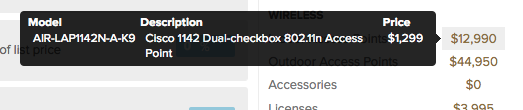
The prices are all list, but you can add the appropriate discount into the calculation to get more realistic numbers, because who pays list? 😉
Closing Thoughts
Like a lot of companies out in the Silicon Valley and Bay Area, Meraki employs a fair amount of smart and talented people. Using commodity hardware and some decent software, they appear to have built a nice product set with a management model that is appealing to your small to medium environments. The questions that I find myself asking are where they fit and don’t fit. What environments would they thrive in? Certainly the heavily distributed environments that survive off a single Internet connection are applicable. Retail immediately comes to mind. I don’t doubt their wireless can scale, but until they can handle layer 3 roaming without a link to the MCC, I will remain cautious. This isn’t a controller/controller-less argument on my part. It’s just that any time you rely on something off site to serve a critical function, you better make sure you have more than one way to connect to it. As for the wired switches, I think they would be fine on the edge. Will they build more capable switching platforms in the future? I am guessing that they will. Hard-wired switches don’t have the same dependency on the dedicated link to a management platform like the wireless solution does. As for the security solutions, they appear to be able to scale up to the large network size. Perhaps some in depth testing of the MX platforms would paint a different picture.
As of today, I have a much different opinion of Meraki compared to just a month ago. I like what they are doing with the concept of “cloud” based management of their hardware. It makes it easier to sell to certain organizations that want to run lean IT shops. The Meraki product is easy to install and easy to use, based on my own testing of one of their wireless AP’s and the corresponding management console. Their products are not for everyone. Certain organizations are not going to want to go the route of “cloud” managed hardware. They also don’t have a ton of different hardware options that some organizations will want. That’s the risk you take when running with a model such as theirs. I do think that we’ll see more and more interest in companies like Meraki as IT resources become scarce in the years to come. By resources, I mean people. I look forward to seeing what they will come up with in the future.
Disclaimer: As a delegate for Wireless Field Day 2, my travel, lodging, and meals were paid for by a number of vendors including Meraki. I also received some items from Meraki with their logo on it along with an MR16 access point to keep for testing or personal use. None of this was done with the expectation that I would write or say anything about them.